Windows 2003 Server provides lots of different out of the box firewall options. There is always the basic firewall either used on the NIC card or though routing and remote access. If you have routing and remote access installed, you can also use inbound and outbound filters. There is a third one that is often overlooked. That’s using IPSEC Security policies as a firewall. I personally use this one for my complex firewall requirement for the network card interface connected to my Untrusted Wireless Network.
I have only 3 simple rules for that network
1. Don’t Allow Clients in the Untrusted Wireless Network to connect to anything on the server, not even ping
2. Allow Clients on the Untrusted Wireless Network to connect to the VPN PPTP port and protocol (TCP 1723, IP 47)
3. Allow all connections from my Gateway Router (the DI-604 connected to our Roadrunner) because that router port maps to the server, and the server makes the connection to the correct client/service.
I basically send a range of ports from the router to my server because my router has a limited number of port map entries, and then the server uses port tunnel to connect the ports from the router to the correct clients. The reason I do it this way is because I can use netbios or DNS names in port tunnel and not have to resort to IP addresses only, like in the router config. This way if a computer changes IP addresses on my network, the port map still works.
Ok, the first thing you need to do is create a new IPSEC policy. Goto Administrative tools, and then Local Security Policy or Domain Controller Security Policy. Right click on IP Security Policies and click “Create IP Security Policy”. I named mine Packet Filter.

Next we will need to add the Block action to block certain traffic. Right click on “IP Security Policies” and click “Manage IP filter lists and filter actions”. Click the “Manager Filter Actions” tab. Click Add, go through the wizard with the defaults, name it block, and select block as the filter action. Ok out of everything.
Now right click on our new Security Policy and click properties. Click add, and go ahead and add the already created filter lists, All ICMP Traffic, and All IP Traffic both with the Permit filter action. I selected LAN for the network type on all of my filter lists.
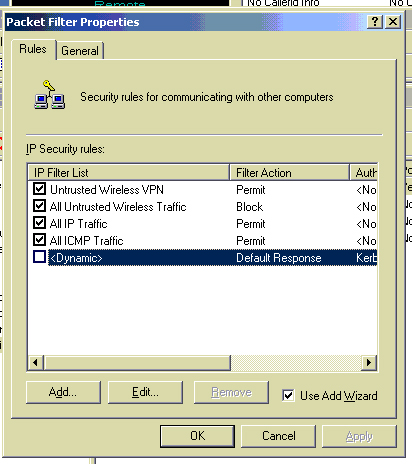
Next you will want to click Add again, but this time click the add button to add a new IP security rule, click through the menu and then click add again to add a new IP filter list. Name it and click Add. Lets create the All Untrusted Wireless Traffic first. I used the settings below. My Untrusted Wireless Network ranges from 192.168.1.1 to 192.168.1.255. Select the source address as a specific IP subnet. The IP address of 192.168.1.0 with a subnet mask of 255.255.255.0 will match every IP address in my Untrusted Wireless Network range. For the destination address I typed in the specific IP address of the network card that is connected to the untrusted network. For the protocol select Any. Finish the wizard and hit ok. Make sure your new IP filter list is selected in the list and click next. Select our new Filter Action of Block and finish the wizard.

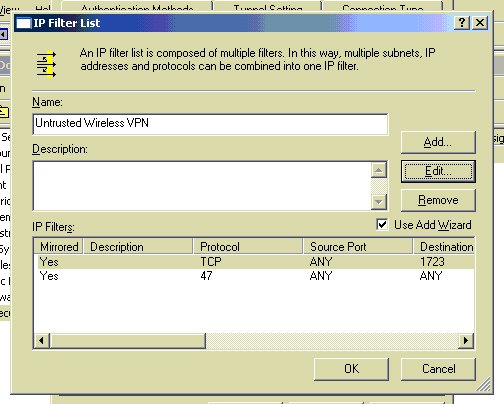
Next we’ll create the Untrusted Wireless VPN IP filter list. Using the same precedure above to create a IP filter list, use the same settings above for the source and destination but this time use these settings below for the protocol. Notice I added two IP filters to this IP filter list. That’s because PPTP VPN requires a TCP port of 1723 and it uses it’s own protocol called GRE, that is IP Protocol 47. When selecting the protocal for this one, select other, and type in 47. Assign this new IP filter list the Permit filter action.
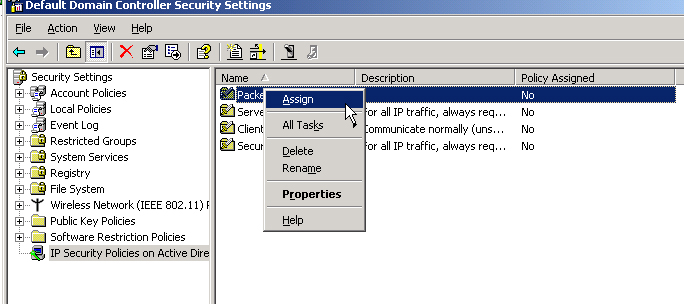
Lastly, we need to assign this IP Security Policy. Right click on the policy and click assign.
That’s it. Now all your traffic from your router should be allowed while no traffic from any wireless client is allowed except for if they are using VPN to connect to the server. I used the network monitor to determine that the source IP address from my router to my server was actually the routers external IP address (the one assigned by Roadrunner). That’s why I don’t need an extra policy specifing the internal IP address of my router to be allowed. If your router behaves differently, just add a ip filter list that matches your routers specific IP address and set the action to permit. Notice that you don’t have to worry about ordering the IP filter lists, it does that automatically for you.
This does not control what your wireless clients can and can’t do on the internet. This just prevents someone from hacking your less secure wireless network and then hacking your server to get access to the trusted network. So if someone does hack your wireless network, all they will be able to do is get internet access, they will think they are the only computer on the network and will be completely unaware of the trusted network unless they happen to be scanning IP addresses on the VPN port 1723. Then they will be suspecious but still will be unable to gain access to your trusted network.